Discover the Perks of LinkDaddy Universal Cloud Storage for Your Service
Discover the Perks of LinkDaddy Universal Cloud Storage for Your Service
Blog Article
Making Best Use Of Information Security: Tips for Getting Your Info With Universal Cloud Storage Provider
In an age where information breaches and cyber risks get on the increase, guarding sensitive info has actually ended up being a vital concern for people and organizations alike. Universal cloud storage space services offer unmatched comfort and availability, yet with these benefits come inherent security risks that need to be attended to proactively. By implementing durable information protection steps, such as encryption, multi-factor verification, routine back-ups, accessibility controls, and monitoring procedures, customers can dramatically enhance the defense of their data stored in the cloud. These methods not just fortify the honesty of details however additionally instill a sense of confidence in entrusting critical information to shadow systems.
Importance of Information File Encryption
Information encryption offers as a fundamental pillar in protecting delicate information stored within universal cloud storage space services. By inscribing data as though just accredited celebrations can access it, security plays a vital duty in protecting secret information from unapproved gain access to or cyber hazards. In the realm of cloud computing, where data is commonly sent and kept across different networks and servers, the demand for robust file encryption systems is vital.

In addition, compliance guidelines such as the GDPR and HIPAA require information file encryption as a way of safeguarding sensitive info. Failure to stick to these requirements might lead to severe consequences, making information security not just a security step yet a lawful need in today's electronic landscape.
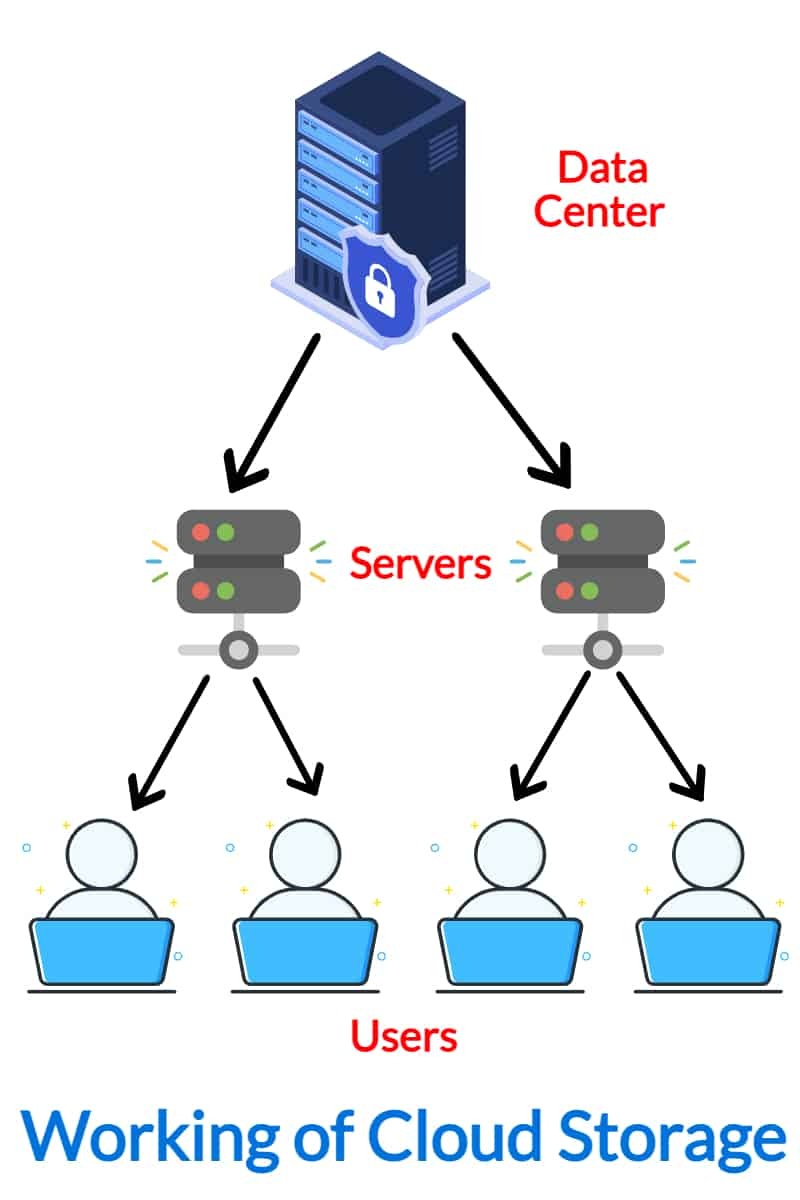
Multi-Factor Authentication Approaches
In boosting safety and security procedures for global cloud storage solutions, the execution of robust multi-factor verification strategies is vital. Multi-factor verification (MFA) includes an extra layer of safety by needing customers to offer numerous forms of verification before accessing their accounts, substantially reducing the danger of unapproved gain access to. Typical factors used in MFA consist of something the user knows (like a password), something the individual has (such as a mobile phone for getting verification codes), and something the user is (biometric information like finger prints or face recognition) By combining these elements, MFA makes it a lot harder for destructive actors to breach accounts, also if one aspect is jeopardized.
To maximize the efficiency of MFA, it is crucial to pick authentication elements that vary and not conveniently replicable. Additionally, normal tracking and updating of MFA setups are important to adjust to advancing cybersecurity hazards. Organizations should likewise inform their users on the importance of MFA and supply clear guidelines on just how to establish up and use it securely. By executing solid MFA strategies, organizations can dramatically boost the safety of their data kept in global cloud solutions.
Normal Information Backups and Updates
Provided the essential duty of securing data integrity in universal cloud storage services with robust multi-factor authentication approaches, the next important element to address is ensuring normal data back-ups and updates. Normal information backups are crucial in reducing the risk of information loss as a result of various variables such as system failures, cyberattacks, or unintended removals. By backing up information consistently, organizations can recover details to a previous state in instance of unanticipated occasions, consequently preserving service continuity and protecting against substantial interruptions.
Moreover, remaining up to date with software program updates and security patches is equally crucial in enhancing information safety within cloud storage services. These updates commonly include fixes for susceptabilities that cybercriminals might exploit to gain unapproved access to our website sensitive information (universal cloud storage). By immediately using updates supplied by the cloud storage provider, organizations can strengthen their defense reaction and guarantee that their data stays safe and secure from developing cyber hazards. Essentially, routine information back-ups and updates play an essential duty in strengthening data security procedures and securing critical info saved in global cloud storage space solutions.
Applying Strong Gain Access To Controls
Accessibility controls are important in preventing unauthorized accessibility to sensitive information saved in the cloud. By applying solid access controls, companies can make certain that only licensed personnel have the necessary permissions to view, modify, or delete information.
One efficient way to impose accessibility controls is by using role-based access control (RBAC) RBAC appoints specific functions to users, giving them access rights based upon their role within the organization. This technique ensures that users only have access to the data and functionalities needed to perform their task obligations. Additionally, applying multi-factor verification (MFA) includes an additional layer of safety and security by requiring individuals to offer several types of verification before accessing sensitive information.
Surveillance and Bookkeeping Data Access
Building upon the foundation of solid gain access to controls, reliable tracking and bookkeeping her response of information accessibility is critical in maintaining data security integrity within global cloud storage solutions. Tracking information gain access to entails real-time monitoring of that is accessing the data, when they are accessing it, and from where. Bookkeeping data access involves assessing logs and documents of data accessibility over a particular duration to ensure conformity with safety plans and laws.
Verdict
To conclude, protecting information click this site with global cloud storage services is critical for shielding delicate info. By applying data encryption, multi-factor verification, routine backups, solid gain access to controls, and monitoring data gain access to, organizations can decrease the danger of data violations and unauthorized access. It is vital to focus on information safety gauges to ensure the confidentiality, honesty, and accessibility of information in today's electronic age.
Report this page